All about the Snowflake cyberattack

For some, the hacker attack suffered by Snowflake, which provides cloud storage services, is already one of the largest and most important ever disclosed. The company plays it down but more and more customers are emerging who have been damaged by the pirates' work. And they are all very large companies, with millions of users' data
As the hours pass, the cyberattack on Snowflake, a significant player in the cloud storage services landscape, is taking on increasingly serious contours, with the theft and resale on the black market of large quantities of private and sensitive data which would concern a growing number of companies. entrepreneurial, active in a variety of fields.
The news, now several weeks after the first report which made it possible to discover, probably with delay, the irruption of computer pirates in the Snowflake clouds, is still scarce, an indication of the fact that the technicians have yet to reconstruct the exact extent of the damage . Initially, the company victim of the theft limited itself to declaring that there were two companies involved, but the reconstruction was immediately denied by the sector press .
WHO ARE THE BIG AFFECTED
It all started two weeks ago with the announcement of the ticketing platform Ticketmaster that it had lost 560 million customer data. “Lost” is not the correct term: that data was stolen from her. The stolen goods would consist of names, addresses, telephone numbers and partial credit cards. All kept on Snowflake with the loot ending up on the dark web in record time.
It is not even known whether, without the reporting of a 1.3TB folder of data sold for the sum of 500,000 dollars on hacking forums, those who should have been vigilant would have ever noticed it or would have continued to ignore the fact that in a the first moment was dated back to May 20th.
FROM THE USA TO EUROPE, UNTIL THE AUSTRALIAN ALARM
And it doesn't end here, because from Beverly Hills, where Live Nation Entertainment, the multinational entertainment company behind the stolen portal, is based, the crumbs left by the hackers lead to Boadilla del Monte, in Spain where the Santander banking institution is based, which a few days later it revealed that it had been the victim of the theft of confidential data of its account holders, which were also kept via the cloud services made available by Snowflake and ended up on the deep web.
Two coincidences too suspicious not to wonder if Snowflake had been hacked by hackers. Also because in those very days an alarm launched from the other side of the world, or rather from the Australian government, warned of the threat .
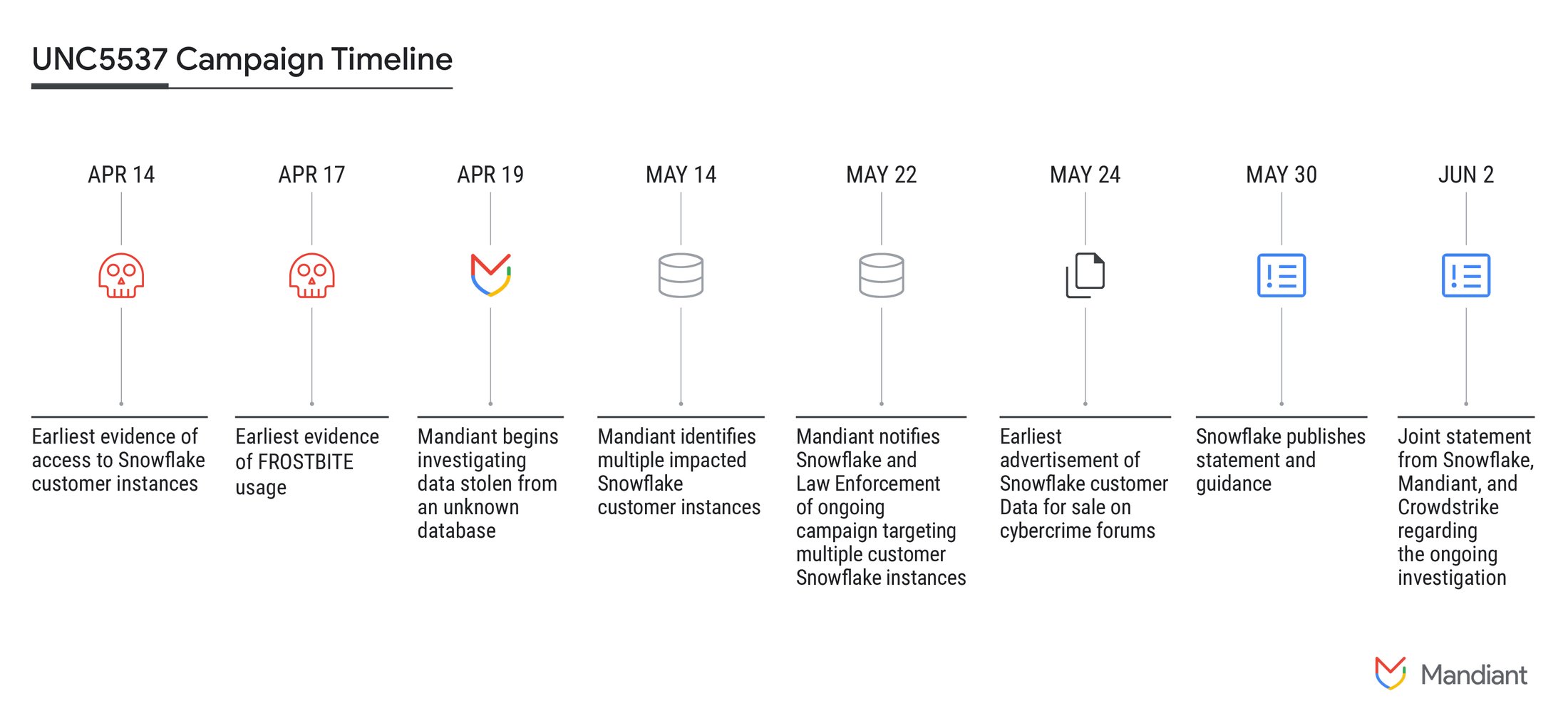
An internal investigation was thus launched entrusted to Mandiant , a computer security company subsidiary of Google, which discovered that the first attacks date back to mid-April and that at least 165 customers, including large groups, were affected by the raid by cyber pirates. .
SOME OF SNOWFLAKE'S CUSTOMERS
However, there is no official information (unofficial yes, as will be seen shortly) on the identity of the other illustrious victims. The list of Snowflake customers is endless and there are many big names, also known in Italy (on the site you can read the logos of Credit Agricole, Axa, Sanofi, Danone, Canal+, Instacart, Bonfiglioli, KraftHeinz, Betclic, Novartis, etc. …), therefore it is difficult to exclude that, as happened in these two weeks, in the next few days the extent of the theft will not further increase its perimeter, branching out into other countries.
In the meantime, reports are increasing. According to the most quoted , the automotive giant Advance Auto Parts and the financial services companies LendingTree and its subsidiary QuoteWizard would also have ended up targets of cyber criminals. The first would have lost the data of 380 million customers (3TB of stolen data would already be on sale on the dark web), the other two 190 million. But there is no officialization. LendingTree, contacted by Wired , "did not respond to multiple requests on alleged violations in the past", the American newspaper reports.
Instead, it confirmed, in the last few hours, that it was the victim of a similar Pure Storage offense, also active in cloud storage systems and services with a workspace on Snowflake which would have exposed information that the company claims to be "telemetry" . The information also reportedly includes names of client companies, LDAP usernames, email addresses and Purity software version numbers. Pure Storage's customers include Meta, Ford, JP Morgan, NASA, NTT, AutoNation, Equinix and Comcast. Meanwhile, Snowflake has had his say on the methods of the theft .
HOW THE SNOWFLAKE SHOT HAPPENED
From what has been reconstructed, the access would have occurred using the company's own utilities, SnowSight and SnowSQL, using an intrusion tool called Frostbite together with access credentials stolen using infostealer tools such as Vidar, Risepro, Redline, Racoon Stealer, Lumma and MetaStealerMalware.
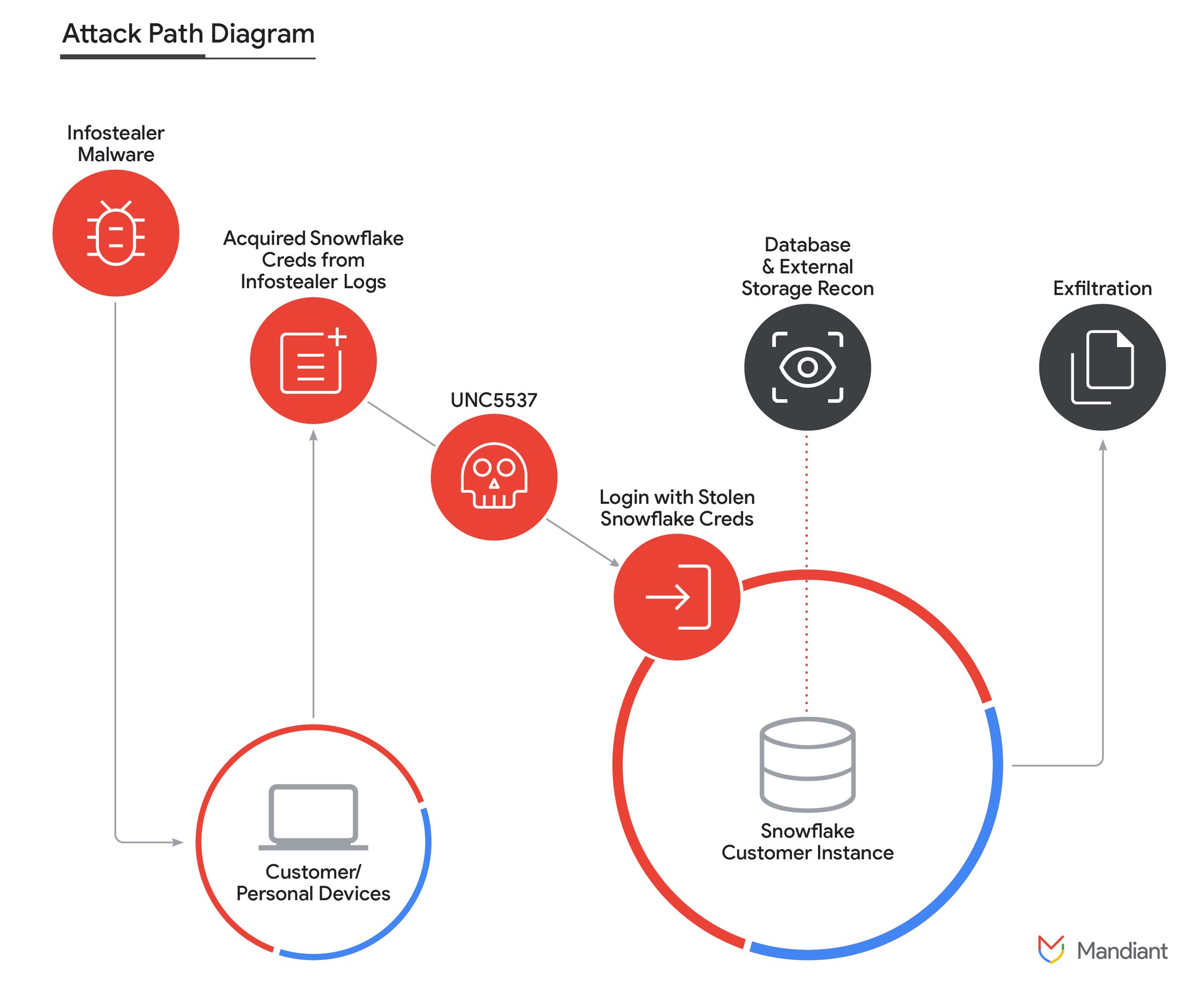
The keys would have been obtained by inoculating malware on systems not necessarily belonging to Snowflake but directly available to customers. The reconstruction of the facts is naturally useful for understanding the weak points of the security system, but above all for identifying civil liability: Mandiant for example underlines that the accounts involved were not configured with multifactor authentication systems, which would have avoided or at least made it more compromise is difficult.
In fact, we are referring to those multi- step authentication steps (first access from a PC, which refers to your mobile phone for reading a code or your fingerprints or other biometric confirmations) which, although fallible (everything can be emulated and digitized) constitute significant problems for computer pirates. An oversight that could take on the form of negligence in court.
Snowflake's blog post states that the internal investigation did not uncover evidence that the attack was "caused by compromised credentials of current or former Snowflake employees," although it did detect access to test accounts. of a former employee, which however did not contain sensitive data. Once the real extent of the damage has been understood, the judicial process will begin to ascertain responsibility and the judges will certainly not be satisfied with a party's expert opinion.
This is a machine translation from Italian language of a post published on Start Magazine at the URL https://www.startmag.it/innovazione/tutto-sul-cyberattacco-a-snowflake/ on Wed, 12 Jun 2024 13:15:58 +0000.
